Simple Steps To Secure Your Smartphone Against Data Theft
You may already know the basics of Internet security and keeping your personal data private while browsing the Web: Use a firewall, don’t open attachments you aren't expecting, and never follow links from strangers. But what about your smartphone? The ease with which security researcher Georgia Weidman was able to infect Android phones with her custom botnet during the 2011 ShmooCon security conference suggests that anyone concerned about the privacy of the personal data stored on their smartphone should think twice before downloading dubious or otherwise untrustworthy apps.
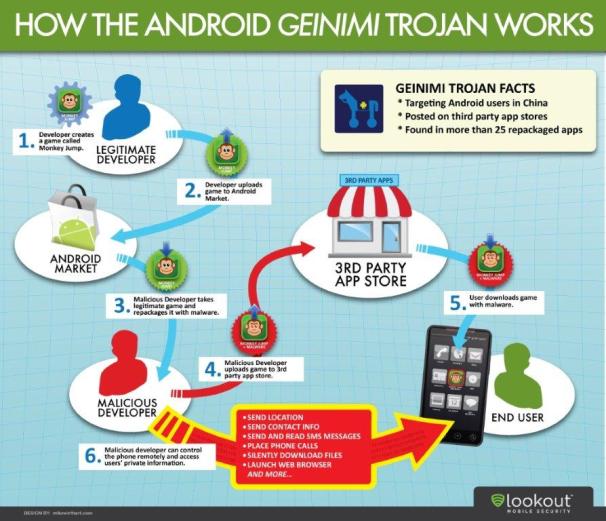
So how does a smartphone botnet spread? First, the victim needs to download a file that contains a bot builder program--a secret snippet of malicious code that will install a bot into the basic operating system of a phone. The infected file could be an app, a piece of music or even an email attachment. “It could be camouflaged in anything at all;” claims Weidman. “Someone might put out a great, functional app that users want. Worse, the app would work as advertised so they wouldn’t suspect it; meanwhile the botnet could be active for years.”
Once your phone is infected, a slave bot program will be installed in the base operating system, beneath the application layer that most users are familiar with. From there these bots can monitor and modify all data sent to and from the phone before you do, allowing the botmaster to command and control your phone without your knowledge. “Since the bot sees everything before the user does, it’s possible to catch private data and forward it elsewhere on the internet,” says Weidman. “What you’ve been doing, who you’re speaking to and where you’ve been.”
Once a botmaster is in control of your phone, the first priority is to spread the infection to as many other users as possible. In the past, mobile botnets have taken advantage of smartphone Internet access to spread malicious code via e-mail; Weidman's Android botnet is dangerous because it communicates and spreads via SMS text messaging instead. Weidman claims hijacking the SMS text messaging service is more battery-efficient and far more subtle than accessing the Internet via a phone’s modem. In addition, it opens up a new attack vector whereby unsuspecting users may receive text messages from an infected friend that contain links to malicious code.
“If I get a text message from a friend with a link that says “hey check this out,” why wouldn’t I trust it?” says Weidman. “If one of my contacts is infected they could be infecting me without knowing it.” Of course, smartphone malware is nothing new; security companies like Symantecand Lookout offer iOS and Android apps that provide malware detection and remote security features like locking or wiping a phone via SMS, but the balkanization of the wireless market among so many different devices and carriers means that it’s often difficult for security companies to keep their apps updated with the latest malware profiles. Worse, most detection apps only scan other applications for malicious code; that approach will catch an infected app, but it won’t do much good if the bot builder program has already overwritten part of the phone’s operating system. It doesn’t matter which operating system either; while Weidman developed her prototype botnet on the Android OS, she claims the bots could work on any smartphone and is currently seeking iOS and Windows Phone 7 devices for testing purposes.
But while Weidman’s security research may seem scary, for the moment it’s just that: research. “If this type of attack becomes prevalent in the future, we will update our software to detect it,” says Kevin Mahaffey, CTO of Lookout Security. “Unless we see malware like this in the wild, we will continue to focus our efforts on existing threats.”
Plus, it’s actually pretty simple to secure your smartphone and keep your data private from a botnet: just remember to take security on your iPhone or Android device as seriously as you do on your laptop. Don’t download apps or files from people you don’t trust, and be wary of any links or files embedded in text messages. Be aware that any file you download to your phone has the potential to be infected, and plan accordingly.








0 comments:
Post a Comment